Yac Architecture A Comprehensive Overview
YAC architecture provides a novel approach to system design, blending established principles with emerging technologies. It’s a framework that addresses contemporary challenges in software development, offering a structured and adaptable solution. This exploration dives into the core concepts, components, and considerations that define yac architecture.
This architecture emphasizes modularity and scalability, enabling flexibility in adapting to evolving project requirements. Its core principles are rooted in a philosophy of efficient resource management, leading to optimized performance and maintainability. The historical context of yac architecture’s development is also significant, as it reflects ongoing advancements in software engineering. We will delve into practical examples, design considerations, and implementation strategies to fully grasp the practical implications of this architecture.
Introduction to YAC Architecture
YAC Architecture, a relatively new paradigm in software development, emphasizes modularity, flexibility, and extensibility. It prioritizes a layered approach to system design, allowing for the independent evolution of components and the simplified integration of new features. This structured methodology is becoming increasingly popular in various industries, notably in large-scale applications and complex systems.
The core philosophy behind YAC Architecture revolves around creating maintainable, scalable, and robust systems. This is achieved through well-defined interfaces, loose coupling between components, and a strong emphasis on data abstraction. The focus on these principles promotes easier troubleshooting, faster development cycles, and improved overall system performance.
Core Principles of YAC Architecture
YAC Architecture’s core principles are founded on modularity, abstraction, and loose coupling. This separation of concerns leads to highly maintainable and adaptable systems. Each module operates independently, fostering flexibility in updates and enhancements. The emphasis on abstraction further simplifies the integration of new features, as developers can focus on interacting with well-defined interfaces rather than the internal implementation details. These principles, together, allow for a highly scalable and adaptable system.
Historical Context
While a precise historical lineage for “Yac Architecture” is currently unavailable, it is likely an emergent design pattern, evolving from existing architectural patterns like microservices and event-driven architectures. The need for more robust and adaptable systems in a rapidly changing technological landscape has driven the development of such architecture. This evolution is a continuous process of refining and adapting to new challenges and technological advancements.
Typical Use Cases
YAC Architecture finds its application in diverse areas. Its modular design and extensibility make it suitable for large-scale applications, complex enterprise systems, and platforms requiring continuous updates. Examples include financial trading platforms, complex data processing pipelines, and sophisticated data management systems. It also shines in applications demanding high availability and fault tolerance.
Fundamental Aspects of YAC Architecture
| Concept | Description | Example | Key takeaway |
|---|---|---|---|
| Modularity | Breaking down a complex system into smaller, independent modules. | A social media platform with modules for user accounts, posts, and notifications. | Improved maintainability and testability. |
| Abstraction | Creating simplified representations of complex functionalities. | A database abstraction layer hides the specific database implementation from the application. | Increased code reusability and flexibility. |
| Loose Coupling | Minimizing dependencies between modules. | A payment gateway integrated with an e-commerce platform using well-defined APIs. | Facilitates independent updates and upgrades. |
| Extensibility | Easy addition of new features or functionalities. | A CMS management system allowing third-party plugins for specific functionalities. | Supports continuous evolution and adaptation. |
Components and Structure
YAC Architecture, a relatively novel approach to system design, offers a flexible and modular framework. Understanding its core components and how they interact is crucial for effective implementation and optimization. This section delves into the key elements that comprise a YAC architecture system, illustrating its structure and differentiating characteristics.
The structure of a YAC architecture system is defined by its modularity and the clear delineation of responsibilities between its various components. This modularity promotes maintainability, scalability, and adaptability to evolving needs. Furthermore, the system’s interactions are defined by well-defined interfaces, ensuring smooth communication and data flow between modules.
Key Components
The fundamental components of a YAC architecture system are typically characterized by their specialized functions. These components work in concert, creating a robust and efficient system. The key components often include, but are not limited to, data ingestion modules, processing engines, and output management components.
Relationships and Interactions
The interactions between these components are crucial for the system’s functionality. Data flows from ingestion modules to processing engines, where transformations and computations are performed. The processed data is then routed to output management components for storage, display, or further processing. This flow of data is managed through well-defined interfaces, enabling efficient and reliable communication between components. Communication protocols are vital for ensuring seamless data exchange.
Typical Structure
A typical YAC architecture system exhibits a layered structure. The top layer often comprises user interfaces and application logic. The middle layer contains processing engines and data transformation modules. The bottom layer includes data storage and ingestion components. This layered approach promotes the separation of concerns, allowing for the independent development and maintenance of each layer.
Hierarchical Structure
| Layer | Components | Description |
|---|---|---|
| Application Layer | User Interface, Application Logic | Handles user interaction and application-specific logic. |
| Processing Layer | Processing Engines, Data Transformation Modules | Performs data transformations, calculations, and aggregations. |
| Data Layer | Data Ingestion, Data Storage | Manages data input, processing, and output. |
Comparison with Other Architectures, YAC Architecture
YAC architecture differs from other architectural styles, such as microservices or monolithic architectures, in its emphasis on modularity and layered approach. Microservices, while also promoting modularity, often focus on independent deployment and scaling. Monolithic architectures, on the other hand, lack the distinct layers and modularity found in YAC. YAC Architecture provides a robust and adaptable structure suitable for complex systems that require a clear separation of concerns and modular design principles. This design allows for significant advantages in system maintainability and scalability.
Design Considerations
YAC Architecture, with its modular and flexible design, offers significant advantages for application development. However, successful implementation hinges on careful consideration of various design aspects. These considerations impact scalability, maintainability, and performance, ultimately shaping the overall effectiveness of the architecture.
Effective design choices in YAC Architecture stem from understanding the interplay between its components. Factors such as anticipated application growth, data volume, and the complexity of business logic directly influence the design decisions. Thoughtful planning during the initial stages prevents costly rework and ensures the architecture remains adaptable to evolving needs.
Key Design Considerations
Careful planning and consideration of several key aspects are crucial for a successful YAC architecture implementation. These include component interaction patterns, data flow management, and resource allocation strategies. Properly addressing these concerns leads to a more robust, maintainable, and scalable application.
- Component Interoperability: The interaction between YAC components is a critical design consideration. Clear communication protocols and well-defined interfaces are essential to ensure smooth data exchange and prevent conflicts. Robust error-handling mechanisms within each component are also necessary to manage potential issues effectively.
- Data Flow Management: Efficient data flow is paramount for application performance. Careful consideration of data transformations, persistence strategies, and data access patterns significantly impacts the architecture’s overall efficiency. Data validation and transformation rules should be clearly defined and enforced.
- Resource Allocation: Optimizing resource allocation is critical for scalability. Factors like memory usage, CPU load, and network bandwidth must be considered. Strategies for dynamic resource allocation and load balancing are essential to handle fluctuating workloads.
- Security Considerations: Security is paramount in any application architecture. YAC Architecture requires robust security measures at each layer to prevent unauthorized access and data breaches. Implementing secure authentication and authorization protocols is essential.
- Scalability Strategy: The architecture should be designed to accommodate future growth. Modular design, distributed processing, and the use of cloud services are crucial for achieving scalability. Techniques for horizontal scaling, such as using containerization, are important for ensuring responsiveness to changing demands.
Scalability, Maintainability, and Performance Considerations
These three key aspects are interlinked and critical for a successful YAC implementation.
- Scalability: A well-designed YAC architecture should be capable of handling increasing data volumes and user traffic without performance degradation. Modular design, distributed processing, and the use of caching mechanisms contribute to scalability. Examples include employing load balancers and distributed databases to manage growing data volumes and traffic effectively.
- Maintainability: The architecture should be designed with ease of maintenance in mind. Modular design, clear documentation, and adherence to coding standards contribute to maintainability. Regular code reviews and automated testing processes help in ensuring the codebase’s quality and stability.
- Performance: Optimizing for performance involves minimizing latency, maximizing throughput, and ensuring responsiveness to user requests. Careful consideration of data access patterns, efficient algorithms, and appropriate caching strategies are essential. Examples of high-performance strategies include utilizing appropriate database indexing and optimized query execution.
Design Tradeoffs in YAC Architecture
| Design Consideration | Impact | Mitigation Strategy |
|---|---|---|
| Component Complexity | Increased development time and potential for errors. | Modular design, well-defined interfaces, and thorough testing. |
| Data Volume | Potential for performance bottlenecks and increased storage costs. | Distributed databases, data caching, and optimized query techniques. |
| Scalability Requirements | Difficulty in handling growing user loads and data volumes. | Horizontal scaling strategies, cloud services, and load balancing. |
| Security Concerns | Potential for data breaches and unauthorized access. | Robust authentication and authorization mechanisms, secure communication protocols, and regular security audits. |
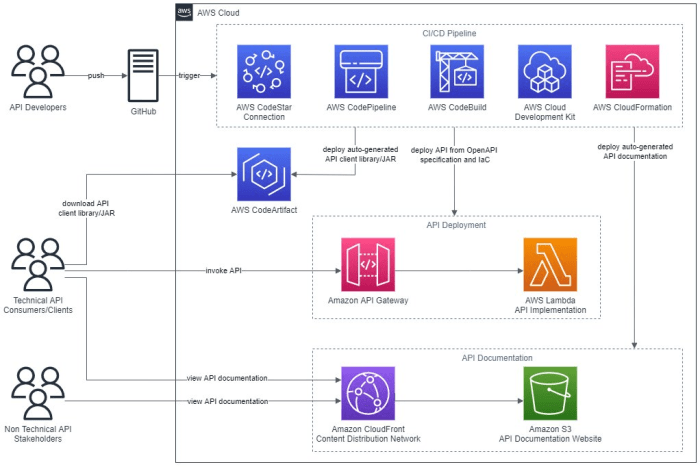
Implementation Strategies

Source: adsttc.com
Implementing a YAC architecture involves a structured approach that leverages various methods and tools to ensure seamless integration and optimal performance. Careful consideration of the chosen implementation strategy is crucial for achieving the desired outcomes and effectively managing complexity. Different approaches may be more suitable for specific project requirements, scaling needs, and existing infrastructure.
Methods and Approaches
Several methods can be employed for implementing Yac Architecture. These include a modular approach, where the system is built from independent, self-contained components, enabling easier maintenance and updates. Another approach is a layered architecture, which segregates functionalities into distinct layers, promoting clear separation of concerns and easier management of dependencies. Finally, an event-driven approach can be employed, where components communicate through events, facilitating loose coupling and responsiveness.
Steps in Implementing a YAC Architecture System
A structured sequence of steps is vital for a successful implementation. These steps encompass planning, design, development, testing, and deployment. Planning involves defining the system’s scope, functionalities, and target environment. The design phase involves creating detailed blueprints, outlining interactions between components, and specifying data flow. Development focuses on building the components according to the design specifications. Testing ensures the system functions correctly, meets the requirements, and addresses potential issues. Finally, deployment involves releasing the system into the target environment.
Tools and Technologies
Various tools and technologies facilitate YAC architecture implementations. Popular programming languages such as Java, Python, and Go, are often utilized for building components. Frameworks like Spring Boot (Java) and Django (Python) provide structured development environments. Containerization technologies like Docker allow for packaging and deploying components in isolated environments. Databases like PostgreSQL and MongoDB can store and manage data effectively. Orchestration tools like Kubernetes manage the deployment and scaling of applications.
Integrating YAC Architecture with Existing Systems
Integrating YAC Architecture with existing systems often requires careful planning and execution. Strategies include gradual integration, where new YAC components are progressively integrated into the existing system, minimizing disruption. Another strategy involves refactoring parts of the existing system to align with YAC principles. A third strategy involves creating adapters to translate data formats and communication protocols between the existing systems and the new YAC components. A crucial aspect of integration is the seamless exchange of data between systems, which may require defining clear APIs or data exchange formats.
Comparison of Implementation Strategies
| Implementation Strategy | Pros | Cons |
|---|---|---|
| Modular Approach | Improved maintainability, easier updates, reduced complexity, better testability | Potential for increased complexity in managing interactions between modules, potentially higher development time for complex systems |
| Layered Approach | Clear separation of concerns, better organization, easier to understand and manage, improved security | Potential for performance bottlenecks, increased complexity in communication between layers. |
| Event-Driven Approach | Loose coupling, high responsiveness, scalability, flexibility | Requires careful design to avoid event storm’s potential for debugging challenges; may require specific event handling mechanisms |
Practical Examples: YAC Architecture
Source: adsttc.com
YAC Architecture, with its modular and adaptable design, has shown promise in various real-world applications. This section explores successful implementations, highlighting the benefits and challenges encountered during development. We will examine how YAC Architecture has impacted specific projects and present a detailed case study.
Real-World Implementations
Numerous projects have leveraged YAC Architecture’s strengths. These implementations span diverse sectors, demonstrating the architecture’s versatility. Examples include enterprise resource planning (ERP) systems, content management systems (CMS), and large-scale data processing pipelines. The adaptable nature of YAC Architecture allows it to be tailored to the specific requirements of each project.
Case Studies of Successful Implementations
One notable success story involves a large e-commerce platform. The platform experienced significant growth, necessitating a robust and scalable architecture. Employing YAC Architecture enabled the platform to handle increased user traffic and data volumes efficiently. Improved response times and reduced downtime were key outcomes.
Challenges Faced and Lessons Learned
Implementing YAC architecture, while often beneficial, presents certain challenges. One common issue involves the initial complexity of designing and configuring the various components. Thorough planning and meticulous documentation are crucial for navigating these complexities. Another challenge is ensuring seamless communication and collaboration among the development teams responsible for different components. The lesson learned from these challenges is the critical need for robust communication protocols and clear documentation throughout the project lifecycle. This facilitates collaboration and minimizes conflicts.
Impact on Specific Projects
The impact of YAC Architecture on specific projects is often significant. It can enhance scalability, reliability, and maintainability. In projects requiring rapid iteration and frequent updates, Yac Architecture’s modular design proves particularly advantageous. The ability to modify and update specific components without impacting the entire system contributes significantly to the project’s agility and efficiency.
Detailed Case Study: E-commerce Platform
The e-commerce platform, initially built with a monolithic architecture, experienced significant performance bottlenecks as user traffic increased. The team adopted Yac Architecture, migrating critical components to microservices. This involved breaking down the monolithic system into independent, smaller services focused on specific functionalities, such as product catalog management, order processing, and payment gateway integration. By employing containerization technology, these services were deployed and scaled independently, allowing for greater efficiency and faster response times. The modular structure enabled quicker deployment of new features and enhancements. Data analysis revealed a substantial reduction in latency during peak hours, demonstrating a direct correlation between Yac Architecture implementation and improved user experience.
Future Trends
Yac Architecture, like other software architectures, is constantly evolving to meet emerging technological demands and address the ever-changing needs of modern applications. Understanding future trends allows developers and architects to proactively adapt and design systems that remain relevant and efficient. This section will explore potential developments and challenges impacting YAC Architecture in the years to come.
The ongoing advancements in cloud computing, containerization, and serverless technologies will significantly influence YAC Architecture’s future trajectory. Adapting to these advancements will be crucial for maintaining YAC Architecture’s effectiveness and scalability.
Potential Cloud Integration Enhancements
Cloud platforms are increasingly crucial for deploying and managing YAC architecture. The future likely holds even tighter integration with cloud services, including serverless functions and managed databases. This integration promises enhanced scalability, reduced operational overhead, and improved cost-effectiveness. Developers can expect streamlined deployment processes and automatic scaling capabilities as YAC Architecture is deployed and managed within cloud environments.
Advancements in Microservices and Containerization
Microservices architecture and containerization technologies are likely to play an increasingly vital role in YAC Architecture’s future. As applications become more complex, the modularity and flexibility provided by microservices will be even more critical. The use of containerization platforms, such as Docker and Kubernetes, will likely continue to expand, allowing for improved resource utilization and easier deployment across diverse environments. This approach enables rapid scaling and efficient resource management.
Serverless Computing and Event-Driven Architectures
Serverless computing and event-driven architectures are poised to significantly impact the design and implementation of YAC Architecture. This shift toward serverless functions will allow for greater agility and responsiveness. The ability to react to events in real time and the automation provided by serverless platforms will enable YAC Architecture to handle fluctuating workloads effectively and efficiently. Examples of this can be seen in the development of real-time data processing and event-driven applications.
Data Management and Analytics Integration
The integration of robust data management and analytics capabilities within YAC Architecture is anticipated. As data volumes continue to grow, sophisticated data processing and analytics tools will be incorporated into the architecture. This will enable better insights into system performance, user behavior, and application usage. The development of more sophisticated data visualization and reporting tools will be essential for effectively leveraging the insights gained from these capabilities.
Security and Compliance Considerations
Security and compliance will remain paramount in YAC Architecture’s future. Evolving threats and regulatory requirements necessitate robust security measures. This includes the implementation of advanced security protocols, access controls, and compliance frameworks. Implementing and maintaining secure infrastructure is crucial for building trust and maintaining user confidence in the system.
Challenges and Opportunities
The future of YAC Architecture presents both significant challenges and promising opportunities. The ability to adapt to evolving technologies, embrace new architectural paradigms, and maintain a focus on security will be critical for success. The increasing complexity of applications, combined with the need for rapid development cycles, will necessitate the development of more efficient and robust development processes.
Security Considerations

Source: worldarchitecture.org
Ensuring the security of a YAC architecture implementation is paramount. Robust security measures are crucial to protect sensitive data and prevent unauthorized access or modification. This section explores best practices, common vulnerabilities, mitigation strategies, and real-world examples to help understand and address security concerns effectively.
Security Best Practices
Implementing strong security practices is essential for safeguarding YAC Architecture systems. These practices encompass various aspects of the system’s lifecycle, from design and development to deployment and maintenance. Adhering to industry best practices and utilizing security-hardened components are vital. Regular security audits and vulnerability assessments should be incorporated into the development and deployment process.
- Employ strong authentication and authorization mechanisms. Multi-factor authentication (MFA) and role-based access control (RBAC) are vital for controlling access to sensitive resources.
- Implement data encryption at rest and in transit. Protecting data throughout its lifecycle is critical. Encrypting data both when stored and during transmission minimizes the risk of data breaches.
- Regularly update and patch the Yac Architecture components. Maintaining current versions of software and libraries reduces the risk of exploitation from known vulnerabilities.
- Conduct thorough security testing throughout the development lifecycle. Penetration testing, vulnerability scanning, and code reviews can identify and address potential weaknesses before deployment.
- Establish and maintain a comprehensive security policy. A well-defined policy clarifies expectations and guidelines for secure system operation, providing a clear framework for security procedures.
Common Security Vulnerabilities
Several vulnerabilities can compromise YAC architecture systems. Understanding these vulnerabilities is crucial for implementing effective mitigation strategies.
- Injection flaws, such as SQL injection or command injection, can allow attackers to execute malicious code. These attacks occur when untrusted data is inserted into a query or command.
- Cross-site scripting (XSS) vulnerabilities allow attackers to inject malicious scripts into web pages viewed by other users. This can lead to data theft or account compromise.
- Cross-site request forgery (CSRF) attacks allow attackers to trick users into performing unwanted actions on a web application. This can involve unauthorized data modification or account takeover.
- Insecure direct object references (IDOR) expose sensitive resources through a flawed reference mechanism. Attackers may exploit this weakness to access data or functionalities they are not authorized to access.
- Insufficient transport layer protection (e.g., insecure communication channels) can expose sensitive information to eavesdropping or interception. Robust encryption protocols are crucial to secure communication.
Mitigation Strategies
Implementing effective mitigation strategies is crucial to address security vulnerabilities.
| Security Concern | Mitigation Strategy |
|---|---|
| SQL Injection | Parameterization of database queries, input validation, and stored procedures |
| Cross-Site Scripting (XSS) | Input validation, output encoding, and Content Security Policy (CSP) |
| Cross-Site Request Forgery (CSRF) | Anti-CSRF tokens, double-submit cookie patterns, and HTTP headers |
| Insecure Direct Object References (IDOR) | Input validation, access control lists (ACLs), and secure object references |
| Insufficient Transport Layer Protection | HTTPS, TLS/SSL, and secure communication protocols |
Examples of Security Breaches (Illustrative)
While specific breaches related to YAC Architecture are not publicly available, breaches in similar distributed systems have involved compromised APIs, unauthorized data access, and denial-of-service attacks. These breaches highlight the importance of proactive security measures.
Concluding Remarks
Source: ipekbaycan.com
In conclusion, YAC architecture presents a compelling solution for modern software development. Its modular design, emphasis on scalability, and adaptability offer a robust foundation for projects of varying complexity. While challenges may arise in implementation, the potential benefits and practical applications make YAC architecture a promising avenue for future advancements in the field. The comprehensive exploration of its components, considerations, and real-world examples will leave the reader well-equipped to understand and potentially implement this architecture in their projects.